Designing Threat Model for Kubernetes
The workloads operating in containers in the cluster on Kubernetes, like any other cloud computing platform, require many levels of security to stop malicious assaults from both outside and from within. Kubernetes, which works as an orchestration platform, has an influence on several runtime security operations, including authentication, authorization, logging, and resource isolation, as well as more sophisticated controls like workload allocation and network segmentation. In further detail, this paper discusses various threat types and concerns as well as recommended security practices for successful Kubernetes implementation. The kind of applications that are used in the cluster will determine the level of danger in the surrounding area.
What is Threat Modeling
Finding vulnerabilities, defining goals, and devising countermeasures to either avoid or lessen the impact of cyber-attacks against the system are all part of the threat modeling process, which is a way to optimize network security. The security or development team uses threat modeling to better identify the potential dangers to a specific system or deployment.
A distributed system with many parts, Kubernetes is complicated. It’s critical to comprehend how various components interact with one another and provide answers to issues like these to conduct an efficient security test.
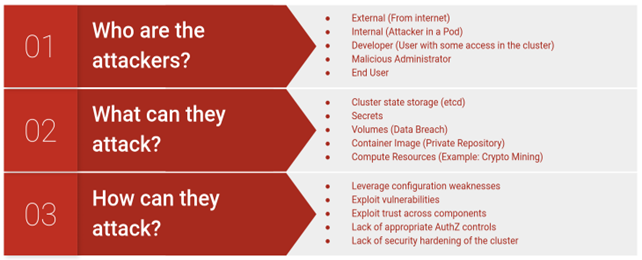
Why is a threat model required?
Any system or process that handles sensitive data or is mission-critical can benefit from threat modeling to determine its security needs. It is a methodical and organized procedure that looks for possible vulnerabilities or weaknesses to lower the risk to IT resources. Early security fault detection helps avoid costly and time-consuming redesigns by identifying complicated threats and data flows for crucial assets.
Threat modeling benefits
Threat modeling has several key benefits:
- Ensures that resources dedicate time and attention to effectively rank risks. To ensure that the solutions are as efficient as possible, this priority may be used while planning, creating, and implementing security.
- Keeps defenses up to date with changing threats. If this does not happen, systems and data may become exposed to fresh risks.
- Supports teams and develops new tools or software. It aids teams in recognizing potential vulnerabilities in tools and apps considering available security measures.
- Assists development teams in setting priorities for software patches based on the gravity and effect of potential risks.
Kubernetes Threat Models
External attacks: All networked systems are subject to this hazard. This is an example of an assault on a Kubernetes cluster where an attacker gains access to the system or compromises some security measures.
Compromised containers or nodes: When malicious containers or malicious nodes are present in the Kubernetes environment or a cluster, what effect does it have on the other nodes or the cluster as a whole?
Compromised credentials: What happens to the cluster if a Kubernetes administrator’s credentials are stolen?
Misuse of legitimate privileges: Systems are configured incorrectly, controls are insufficient, or operations are not closely supervised.
Compromised Containers
Reduce the effect of compromised containers by isolating Kubernetes components using namespaces or network segmentation and managing access controls.
External attacks to the cluster
Make sure that just the essential Kubernetes services are exposed, to reduce the risk of external attacks. For any exposed services, always impose authentication and set up the proper network security settings.
Compromised Credentials/ Least privilege access
Whenever any user credentials are compromised, malicious users will have access to the entire cluster. To reduce the impact on the cluster, we should regulate the privileges religiously.
Improper use of privileges
In order to prevent malicious users from accessing the system in the event that network policies are implemented improperly and do not restrict access to namespaces, we need to make sure that all rights and access permissions are hardened.
Threat modeling methodologies
There are several approaches you can utilize while undertaking threat modeling.
STRIDE threat modeling
A threat model called STRIDE was developed by Microsoft engineers to help in the process of finding dangers in a system.
STRIDE stands for the dangers it addresses, which are:
- Spoofing — pretending to be someone else by using a user or a system
- Tampering — attackers limit modules or code
- Repudiation — Threatening incidents are not recorded or watched.
- Information disclosure — data is exposed
- Denial of service (DoS) — traffic overload prevents authorized usage of services or components
- Elevation of Privilege — In order to have more influence over a system, attackers offer themselves extra privileges.
Common Vulnerability Scoring System (CVSS)
This method is intended to assist security teams in evaluating risks, determining implications, and locating existing defenses. Additionally, it enables security experts to accurately evaluate and use threat intelligence created by others.
The influence of the risk factor owing to the passage of time since the vulnerability was initially identified is taken into consideration by CVSS, along with the threat’s fundamental characteristics. Additionally, it has provisions that enable security teams to explicitly alter risk assessments in accordance with different system setups.
Visual, Agile, and Simple Threat (VAST)
The automated threat modeling technique known as Visual, Agile, and Simple Threat (VAST) was developed using the Threat Modeller platform. To produce accurate, usable data and preserve scalability, large businesses employ VAST across their whole infrastructure.
VAST may be integrated into the DevOps lifecycle and assist teams in recognizing different operational and infrastructural issues. Two different threat models must be created in order to use VAST:
- Operational threat model — depicts the danger from the attacker’s point of view via a data-flow diagram.
- Application threat model — utilizes a process-flow diagram to depict the threat’s architectural component.
Security Cards
The Security Cards methodology relies less on formalized threat modeling techniques and more on free-form brainstorming and original thought. It is intended to assist security teams in planning for less frequent or unusual assaults. This methodology is a useful tool for security teams to learn more about risks and approaches to threat modeling.
The approach makes use of a deck of 42 cards that aid analysts in providing answers to hypothetical questions concerning potential attacks, such as who may launch one, what might drive them, which systems they might target, and how they might carry one out. To mimic potential attacks and go through the organization’s various responses, analysts deal the cards in a sort of tabletop game.